Having to attend BILT, a leadership training for clubs, I had to skip week 6 of Ethical Hacking class. The topic of the lecture was port scanning. For week 7, we tried doing the port scanning. We used nmap and the command used was
nmap -O www.example.com
Since we were testing for pentest.id, the command used was
nmap -O pentest.id
The result was as follows
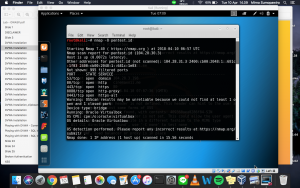
When Mr. Lim showed it in class, the OS shown was Linux. In mine, it said Oracle Virtualbox. Mr. Lim said that the result could be affected by the traffic, meaning that if many people are accessing at the same time the test can give different results. Thinking of that, I tried to do it with another website that my friend made for Web Application final project. The result was as follows
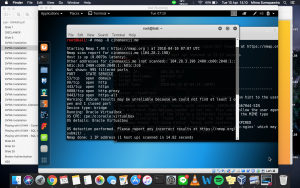
When I did the same command for cinemaxxii.me, the OS result was the same which is Oracle Virtualbox. I thought this was weird because it should give the result of the OS. Instead, it seems like it’s just returning what I am using, which is Virtualbox. I still want to try more because I’m still curious. So I tried using another one of my friend’s website. The result was as follows
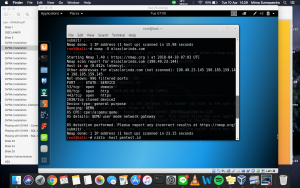
This time, I got a different result. It says the OS is QEMU. When I tried googling it, it turns out that QEMU is a machine emulator. QEMU is similar to Virtualbox, which means that I do not get the answer that I want.
Another tool that we got to try was nikto. The command used was
nikto -host www.example.com
The command is used to target a host. We tried using it for pentest.id and the result was as follows
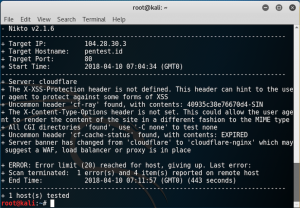
From that test, we can get the target IP and port. We can also see that the website runs on cloudflare. Notice the gap on the 4th line from the bottom. When the command was still running, it was stuck in that line for a moment until it shows ERROR. Mr. Lim said that this may be one of the way cloudflare was protecting the website.
